Revit Guides
Data Management
ELI5
BS EN ISO 19650-5:2020
Organization and digitization of information about buildings and civil engineering works, including building information modelling (BIM) Information management using building information modelling Part 5: Security-minded approach to information management
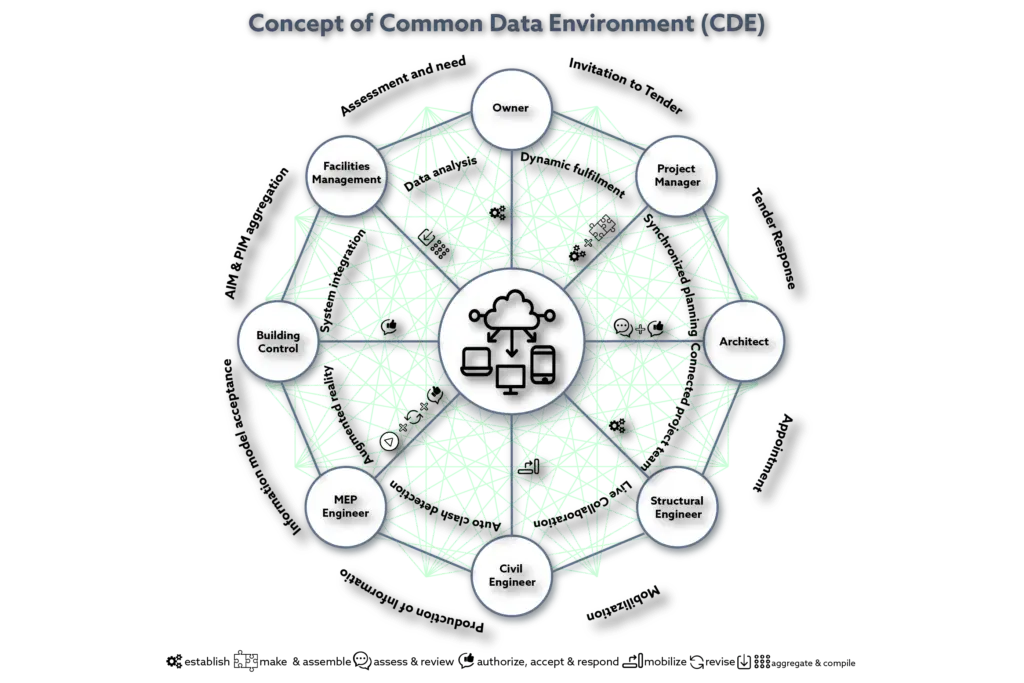
Common Data Environment (CDE)
ELI5-S1: BIM Basics E2: CDE Explained The purpose of using Common Data Environment (CDE) on a project is to provide the right person with the right information at the right
security
state of relative freedom from threat (3.13) or harm caused by deliberate, unwanted, hostile or malicious acts [cited from ISO 19650-5:2020(en), 3.7]
vulnerability
weakness that can be exploited to cause harm [cited from ISO 19650-5:2020(en), 3.15]
BS EN ISO IEC 27000:2020
Information technology – Security techniques – Information security management systems – Overview and vocabulary ISO 27000 is derived from the British Standard 7799, published in 1995 in three parts: BS-7799,
BS 7799‑3:2017
Information security management systemsPart 3: Guidelines for information security risk management (revision of BS ISO/IEC 27005:2011)
System of systems
A system of systems is a collection of many different systems, each with its own characteristics. [1] System theory assumes that certain underlying concepts and principles are applicable to different
System of engagement
The System of Engagement is defined as a platform that manages supported digital engagement, of systems like Browsing, Web Chat, Messaging, videos (Facebook, WhatsApp, TEAMS, ZOOM, Signal, Slack, etc.), various
Security Management Plan
A document (or part of a document) identified in the Information Particulars setting out the security requirements for carrying out the Works in a security-minded way, including any policies, protocols,
Sensitive Information
ELI5-S1 BIM Basics E16_Sensitive Information information, the loss, misuse or modification of which, or unauthorized access to, could:(a) adversely affect the privacy, welfare or safety of an individual or individuals;(b)

